|
Trends
- The top attacker country was China with 174878 unique attackers (24.21%).
- The top Trojan C&C server detected was RedLine with 29 instances detected.
- The top phishing campaign detected was against Facebook accounts with 42 instances detected
Ransomware Dumps of Australian Companies
This week has seen a dramatic increase in data dumps from ransomware attackers. Multiple organisations have had their data dumped on the dark web after suffering ransomware attacks from groups such as Ryuk/Sodinokibi.
Amongst these dumps was Australian transportation and logistics company Toll Group. The ransomware group
claims to have over 200GB of total data, having dumps six parts in the past couple of weeks including data from subsidiaries such as Bowman’s Rail. Ransomware groups continue to develop and divide their skill-sets with the emergence of Ransomware As a Service (RaaS), groups dedicated to initial compromise (initial access brokers)
and the emergence of specialty positions in negotiating ransomware payments. The number of data leak sites continues to grow with Ako, Avaddon, Ragnar Locker, SunCrypt, LockBit, Mount Locker and Clop having individual
dump sites.
Medicare Phishing Campaign
Red Piranha's Crystal Eye XDR has detected a sudden surge in domain registrations with minor variations of
'medicare'. Over 137 domains have been registered in a single day. Most of these domains were a variation of medicarehelpline.com with single letters changed. Common substitutions include replacing I with l (lower case I
and lower case L) as it is difficult to distinguish the difference with many sans-serif fonts. The volume of domains registered suggests that a domain generation algorithm (substitution) has been employed, with whois data showing these domains registered through Aliyun.com (Alibaba Cloud Computing Beijing), based in China.
|
|
|
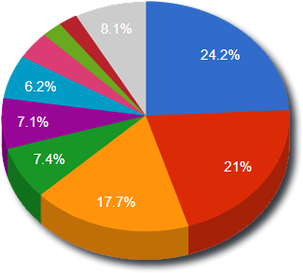
Top Attackers By Country
| China |
174878 |
24.21% |
| United States |
151801 |
21.02% |
| Russia |
127962 |
17.72% |
| Australia |
53472 |
7.40% |
| India |
51278 |
7.10% |
| Germany |
44479 |
6.16% |
| Canada |
27969 |
3.87% |
| Bulgaria |
16648 |
2.30% |
| Panama |
15366 |
2.13% |
| South Korea |
13010 |
1.80% |
| Vietnam |
11002 |
1.52% |
| Nepal |
9525 |
1.32% |
| France |
7550 |
1.05% |
| Brazil |
6490 |
0.90% |
| Colombia |
5348 |
0.74% |
| Iran |
2784 |
0.39% |
| Japan |
2769 |
0.38% |
|
|
|
Top Attackers By Country
|
 |
 China China United States United States Russia Russia Australia Australia India India
|
 Germany Germany Canada Canada Bulgaria Bulgaria Panama Panama Other Other
|
|
|
|
|
|
|
|
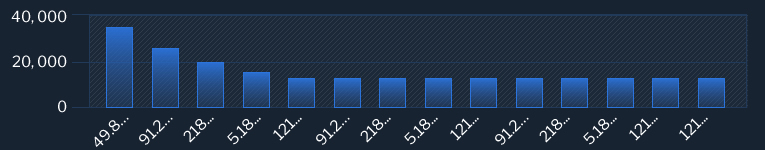
Top Attacking Hosts
| 49.88.112.118 |
32038 |
| 91.241.19.71 |
22643 |
| 91.241.19.59 |
20392 |
| 49.88.112.68 |
16233 |
| 91.241.19.244 |
15364 |
| 218.92.0.206 |
11620 |
| 5.189.153.72 |
10681 |
| 121.182.106.202 |
9900 |
| 155.138.149.180 |
9270 |
| 103.58.144.27 |
9219 |
| 86.162.254.47 |
9051 |
| 94.232.46.100 |
8694 |
| 78.128.112.6 |
8612 |
| 185.55.243.31 |
8112 |
| 185.55.243.27 |
8103 |
| 78.128.112.2 |
8036 |
|
Top Attackers
 |
|
|
|
Top Network Attackers
| 32329 |
United States |
MONKEYBRAINS, US |
| 4134 |
China |
CHINANET-BACKBONE No.31,Jin-rong Street, CN |
| 207566 |
Russia |
HOSTWAY-AS, RU |
| 51167 |
Germany |
CONTABO, DE |
| 4766 |
South Korea |
KIXS-AS-KR Korea Telecom, KR |
| 20473 |
Canada |
AS-CHOOPA, US |
| 63991 |
Nepal |
ARROWNETPVTLTD-NP Arrownet Pvt.Ltd, NP |
| 2856 |
United Kingdom |
BT-UK-AS BTnet UK Regional network, GB |
| 39465 |
Belarus |
UGAVIA-AS, RU |
| 202325 |
Bulgaria |
AS_4MEDIA, BG |
| 12586 |
Germany |
ASGHOSTNET, DE |
|
|
|
|
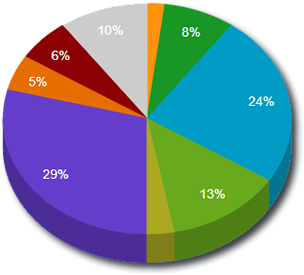
Remote Access Trojan C&C Servers Found
| Amadey |
1 |
217.8.117.102 |
| Anubis |
1 |
119.28.105.61 |
| Azorult |
2 |
104.237.252.41 , 185.208.182.54 |
| CobaltStrike |
8 |
188.227.86.115 , 45.142.215.38 , 45.146.165.140 , 45.146.165.141 , 45.146.165.227 , 84.38.181.217 , 84.38.182.41 , 92.42.14.133 |
| Falcon |
1 |
119.28.105.61 |
| Heodo |
24 |
109.116.245.80 , 110.39.162.2 , 12.184.217.101 , 177.85.167.10 , 181.120.72.110 , 186.146.229.172 , 186.188.212.201 , 190.146.92.48 , 190.147.84.191 , 190.7.217.90 , 221.161.206.22 , 27.78.27.110 , 27.82.13.10 , 37.221.70.250 , 41.231.225.139 , 51.89.36.180 , 74.75.104.224 , 78.125.252.112 , 80.15.100.37 , 81.241.22.161 , 82.208.149.146 , 86.127.212.235 , 94.52.168.188 , 98.150.169.135 |
| LiteHTTP |
1 |
185.243.215.213 |
| Lokibot |
13 |
103.129.98.18 , 104.237.252.41 , 104.237.252.41 , 104.31.66.211 , 163.44.198.61 , 172.67.187.65 , 185.208.182.56 , 185.212.128.225 , 185.243.215.191 , 192.185.91.41 , 204.11.58.39 , 45.252.248.42 , 81.29.143.6 |
| Nexus |
1 |
66.42.81.131 |
| Oski |
1 |
80.89.230.198 |
| Predator |
1 |
185.50.25.27 |
| PurpleWave |
1 |
45.147.197.180 |
| Redirected |
3 |
159.89.6.175 , 207.154.206.177 , 207.154.226.241 |
| RedLine |
29 |
104.198.31.96 , 104.27.130.15 , 109.234.35.30 , 138.124.180.4 , 155.138.201.103 , 162.245.238.120 , 178.20.40.83 , 185.161.209.16 , 185.248.100.191 , 185.45.192.205 , 188.119.112.16 , 3.250.34.72 , 37.1.213.110 , 45.128.150.68 , 45.133.245.129 , 45.142.213.64 , 45.150.67.49 , 45.67.229.13 , 45.67.229.210 , 45.67.229.76 , 45.84.0.155 , 5.253.60.13 , 5.34.180.163 , 62.113.116.146 , 87.251.71.108 , 89.223.25.184 , 91.211.116.133 , 91.235.129.67 , 95.179.148.51 |
| TrickBot |
5 |
185.163.47.157 , 194.5.249.176 , 51.81.112.135 , 66.85.183.5 , 91.200.102.21 |
| Ursnif |
6 |
178.32.27.3 , 185.219.220.75 , 37.221.114.43 , 63.250.33.54 , 79.110.52.173 , 79.110.52.80 |
| Zeus |
1 |
209.133.220.58 |
| Zloader |
1 |
8.208.97.57 |
|
Trojan C&C Servers Detected
 |
 Azorult Azorult CobaltStrike CobaltStrike Heodo Heodo Lokibot Lokibot Redirected Redirected
|
 RedLine RedLine TrickBot TrickBot Ursnif Ursnif Other Other
|
|
|
|
|
|
Common Malware
| ce4395edbbf9869a5e276781af2e0fb5 |
https://www.virustotal.com/gui/file/f059a5358c24cc362c2f74b362c75e02035fdf82f9ffae8d553afee1a271afd0/details |
wupxarch635.exe |
N/A |
W32.Auto:f059a5358c.in03.Talos |
| dd726d5e223ca762dc2772f40cb921d3 |
https://www.virustotal.com/gui/file/432fc2e3580e818fd315583527ae43a729586af5ee37f99f04b562d1eff2a1fd/detection |
ww24.exe |
N/A |
W32.TR:Attribute.23ln.1201 |
| e2ea315d9a83e7577053f52c974f6a5a |
https://www.virustotal.com/gui/file/c3e530cc005583b47322b6649ddc0dab1b64bcf22b124a492606763c52fb048f/detection |
c3e530cc005583b47322b6649ddc0dab1b64bcf22b124a492606763c52fb048f.bin |
N/A |
Win.Dropper.Agentwdcr::1201 |
| 799b30f47060ca05d80ece53866e01cc |
https://www.virustotal.com/gui/file/15716598f456637a3be3d6c5ac91266142266a9910f6f3f85cfd193ec1d6ed8b/detection |
mf2016341595.exe |
N/A |
Win.Downloader.Generic::1201 |
| 8c80dd97c37525927c1e549cb59bcbf3 |
https://www.virustotal.com/gui/file/85b936960fbe5100c170b777e1647ce9f0f01e3ab9742dfc23f37cb0825b30b5/detection |
Eternalblue-2.2.0.exe |
N/A |
Win.Exploit.Shadowbrokers::5A5226262.auto.talos |
|
|
|
|
Top Phishing Campaigns
| Facebook |
42 |
| Other |
1749 |
| Virustotal |
18 |
| Accurint |
1 |
| Google |
11 |
| Halifax |
29 |
| Apple |
1 |
| Amazon.com |
13 |
| RuneScape |
2 |
| Very |
1 |
| Groupon |
1 |
| Rakuten |
2 |
| Microsoft |
14 |
| PayPal |
35 |
| Allegro |
1 |
| Dropbox |
1 |
| DHL |
1 |
| Vodafone |
1 |
| EE |
2 |
| Netflix |
3 |
| Instagram |
2 |
| Blockchain |
1 |
|
|
|
|
Discovered Ransomware Dumps
| Luxottica |
| EWIE |
| Beaver Street Fisheries Inc. |
| Moss Inc. |
| SPIE Group |
| Fisher & Paykel |
| Toll Group |
| Stadler Rail |
| Midwest Express Co |
| Chatham, County, North Carolina |
| AMT Senior Aerospace |
| Mitsubishi Polysilicon America Corporation |
| Salem Town Hall |
|
|
|
|
CVEs with Recently Discovered Exploits
This is a list of recent vulnerabilities for which exploits are available.
CVE-2020-14882
Oracle WebLogic Server Remote Code Execution Vulnerability
Oracle
|
Oracle Weblogic server is exposed to a critical vulnerability. The vulnerability could be exploited by an unauthenticated attacked with a single HTTP request. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle WebLogic Server. Successful attacks of this vulnerability can result in takeover of Oracle WebLogic Server. |
CVSSv3BaseScore:9.8(AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
10/21/2020 |
10/29/2020 |
CVE-2020-14871
Oracle Solaris Remote Code Execution Vulnerability
Oracle
|
Easily exploitable vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Oracle Solaris. While the vulnerability is in Oracle Solaris, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in takeover of Oracle Solaris. |
CVSSv3BaseScore:10.0(AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H) |
10/21/2020 |
10/23/2020 |
CVE-2020-14871
Oracle Solaris Remote Code Execution Vulnerability
Oracle
|
Easily exploitable vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Oracle Solaris. While the vulnerability is in Oracle Solaris, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in takeover of Oracle Solaris. |
CVSSv3BaseScore:10.0(AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H) |
10/21/2020 |
10/23/2020 |
CVE-2020-15999
Google Chrome Freetype Heap Buffer Overflow Vulnerability
Google
|
Google Chrome issued an update announcement for the browser across all platforms. Google confirmed that the "stable channel" desktop Chrome browser is being updated across Windows, Mac, and Linux platforms. As per Google's official sources, this urgent update will start rolling out over the coming few days or weeks. |
CVSSv3BaseScore:8.8(AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H) |
11/02/2020 |
11/06/2020 |
CVE-2020-14750
Oracle WebLogic Server Unauthenticated Remote Code Execution Vulnerability
Oracle
|
Oracle released critical October update to patch CVE-2020-14882 earlier in October. Oracle WebLogic Server has now observed that attackers can now bypass this patch exposing an unauthenticated Remote Code Execution vulnerability. Unauthorized attackers can continue to bypass the WebLogic background login restrictions and control the server even after WebLogic is patched for CVE-2020-14882. |
CVSSv3BaseScore:9.8(AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
11/02/2020 |
11/02/2020 |
CVE-2020-13935
Apache Tomcat WebSocket Denial of Service Vulnerability
Apache
|
The payload length in a WebSocket frame was not correctly validated in Apache Tomcat. Invalid payload lengths could trigger an infinite loop. Multiple requests with invalid payload lengths could lead to a denial of service. |
CVSSv3BaseScore:7.5(AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H) |
07/14/2020 |
10/27/2020 |
CVE-2020-1472
Microsoft Netlogon Elevation of Privilege Vulnerability
Microsoft
|
An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC). An attacker who successfully exploited the vulnerability could run a specially crafted application on a device on the network. To exploit the vulnerability, an unauthenticated attacker would be required to use MS-NRPC to connect to a domain controller to obtain domain administrator access. |
CVSSv3BaseScore:10.0(AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H) |
08/17/2020 |
10/05/2020 |
CVE-2019-4563
IBM Security Directory Server Vulnerability
IBM
|
IBM Security Directory Server does not set the secure attribute on authorization tokens or session cookies. Attackers may be able to get the cookie values by sending a http:// link to a user or by planting this link in a site the user goes to. The cookie will be sent to the insecure link and the attacker can then obtain the cookie value by snooping the traffic. |
CVSSv3BaseScore:5.3(AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N) |
10/29/2020 |
10/30/2020 |
|
|
|
|

