Trends
-
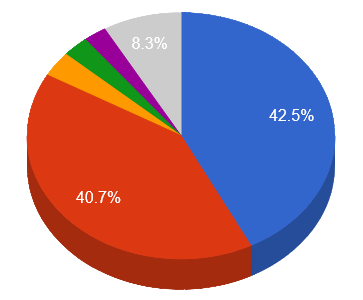
The top attacker country was China with 112942 unique attackers (42.50%).
-
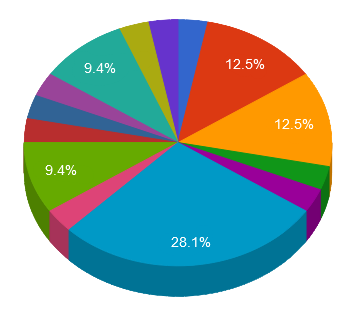
The top Trojan C&C server detected was Lokibot with 9 instances detected.
-
The top phising campaign detected was againts Facebook accounts with 57 instances detected.
1.9 million Pixlr user records were posted for free on forum by hacker.
A threat actor known as "ShinyHunters" has leaked 1.9 million Pixlr user records consisting of email addresses, login names, SHA-512 hashed passwords, and the user's country they signed up for the newsletter and other internal information. Worryingly this data can be used to carry out targeted phishing and credential stuffing cyberattacks.
'ShinyHunters' is renowned for hacking websites and selling stolen user databases at private sales or through data breach brokers. Previously he's been responsible for the data leaks at Minted, Chatbooks, Dave, Promo, Mathway, Wattpad, and many more.
Hacker leaks Database of 77 million Nitro PDF user records
Nitro PDF has experienced a significant data breach. Over 77 million records of the users of their services, including names, email addresses, and bcrypt passwords were leaked on the dark web, earlier today for free.
|
|
|
|
Top Attackers By Country
| China |
112942 |
42.50% |
| United States |
108137 |
40.69% |
| India |
8818 |
3.31% |
| Russia |
7373 |
2.77% |
| France |
6464 |
2.43% |
| South Korea |
4966 |
1.86% |
| Singapore |
4869 |
1.83% |
| Brazil |
4740 |
1.78% |
| Germany |
3668 |
1.38% |
| Paraguay |
777 |
0.29% |
| Thailand |
714 |
0.26% |
| Kyrgyzstan |
662 |
0.24% |
| Ukraine |
655 |
0.24% |
| Algeria |
498 |
0.18% |
| Uruguay |
433 |
0.16% |
|
|
|
Top Attackers By Country
|
 |
 China China United States United States India India Russia Russia France France Other Other
|
|
|
|
|
|
|
|
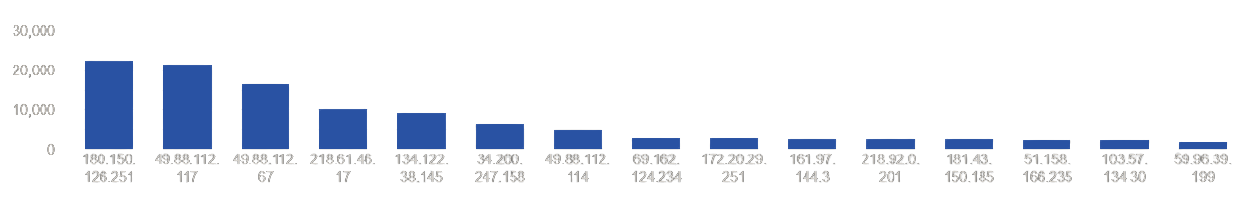
Top Attacking Hosts
| 180.150.126.251 |
22469 |
| 49.88.112.117 |
21538 |
| 49.88.112.67 |
16573 |
| 218.61.46.17 |
10273 |
| 134.122.38.145 |
9243 |
| 34.200.247.158 |
6701 |
| 49.88.112.114 |
4831 |
| 69.162.124.234 |
2854 |
| 172.20.29.251 |
2831 |
| 161.97.144.3 |
2762 |
| 218.92.0.201 |
2660 |
| 181.43.150.185 |
2604 |
| 51.158.166.235 |
2475 |
| 103.57.134.30 |
2371 |
| 59.96.39.199 |
2056 |
|
Top Attackers
 |
|
|
|
Top Network Attackers
| 4134 |
China |
CHINANET-BACKBONE No.31,Jin-rong Street, CN |
| 4837 |
China |
CHINA169-BACKBONE CHINA UNICOM China169 Backbone, CN |
| 14061 |
United States |
DIGITALOCEAN-ASN, US |
| 14618 |
United States |
AMAZON-AES, US |
| 46475 |
United States |
LIMESTONENETWORKS, US |
| 51167 |
Germany |
CONTABO, DE |
| 12876 |
Netherlands |
Online SAS, FR |
| 134033 |
India |
HIREACH-BROADBAND-AS HIREACH BROADBAND PRIVATE LTD, IN |
| 9829 |
India |
BSNL-NIB National Internet Backbone, IN |
|
|
|
|
Remote Access Trojan C&C Servers Found
| AgentTesla |
1 |
64.188.18.218 |
| Amadey |
4 |
146.0.77.110 , 45.143.137.155 , 80.249.147.144 , 80.89.235.60 |
| Azorult |
4 |
104.237.63.179 , 104.28.8.64 , 191.96.225.126 , 5.79.66.145 |
| BlackNet |
1 |
185.136.157.51 |
| DiamondFox |
1 |
165.22.30.153 |
| Lokibot |
9 |
104.148.41.8 , 104.237.252.85 , 167.250.5.6 , 185.238.3.183 , 192.53.126.66 , 208.70.248.230 , 213.159.212.148 , 5.253.63.169 , 95.181.155.66 |
| MassLogger |
1 |
144.91.112.76 |
| Predator |
3 |
141.8.192.93 , 5.23.50.61 , 5.79.66.145 |
| Redirected |
1 |
139.162.150.121 |
| RedLine |
1 |
212.22.77.121 |
| Taurus |
1 |
62.77.159.31 |
| TrickBot |
3 |
18.188.18.65 , 3.15.209.89 , 54.244.106.110 |
| Vidar |
1 |
176.123.10.30 |
| Zloader |
1 |
185.240.102.113 |
|
Trojan C&C Servers Detected
 |
 AgentTesla AgentTesla Amadey Amadey Azorult Azorult BlackNet BlackNet DiamondFox DiamondFox Lokibot Lokibot MassLogger MassLogger
|
 Predator Predator Redirected Redirected RedLine RedLine Taurus Taurus Trickbot Trickbot Vidar Vidar Zloader Zloader
|
|
|
|
|
|
Common Malware
| 8c80dd97c37525927c1e549cb59bcbf3 |
https://www.virustotal.com/gui/file/85b936960fbe5100c170b777e1647ce9f0f01e3ab9742dfc23f37cb0825b30b5/detection |
Eternalblue-2.2.0.exe |
N/A |
Win.Exploit.Shadowbrokers::5A5226262.auto.talos |
| eb20ca63dc3badc1a48072d33bd6428b |
https://www.virustotal.com/gui/file/2c36cb4e1771a04e728d75eb65b05f6875d4eb56df6eb5810af09d0d5e419cd5/details |
1 Total New Invoices-Monday December 14 2020.xlsm |
N/A |
W32.2C36CB4E17-90.SBX.TG |
| 8193b63313019b614d5be721c538486b |
https://www.virustotal.com/gui/file/e3eeaee0af4b549eae4447fa20cfe205e8d56beecf43cf14a11bf3e86ae6e8bd/details |
SAService.exe |
SAService |
PUA.Win.Dropper.Segurazo::95.sbx.tg |
| 7e36752d274e61b9f2b0ee43200fe36d |
https://www.virustotal.com/gui/file/4b8aef15c75ab675acdd9588bbcbd45dcc11a270513badfb21cfdfd92f723b01/details |
Click HERE to start the File Launcher by WebNavigator Installer_ryymehv3_.exe |
WebNavigatorBrowser |
W32.48C6324412-95.SBX.TG |
| 552299482ffa389321df9b05740c1b92 |
https://www.virustotal.com/gui/file/763d0f405ca4a762ce5d27077f3092f295b6504a743f61b88a1de520bcdb3d8a/details |
webnavigatorbrowser.exe |
WebNavigatorBrowser |
W32.763D0F405C-100.SBX.VIOC |
|
|
|
|
Top Phishing Campaigns
| Virustotal |
7 |
| Facebook |
57 |
| Other |
1474 |
| Instagram |
11 |
| Google |
9 |
| PayPal |
23 |
| Vodafone |
3 |
| Itau |
1 |
| RuneScape |
1 |
| Amazon.com |
13 |
| Yahoo |
2 |
| Adobe |
7 |
| AT&T |
1 |
| TSB |
3 |
| Halifax |
30 |
| Microsoft |
3 |
| DHL |
2 |
| Caixa |
1 |
| Three |
4 |
| Netflix |
3 |
| Rakuten |
1 |
| Special |
1 |
| VKontakte |
1 |
|
|
|
|
CVEs with Recently Discovered Exploits
This is a list of recent vulnerabilities for which exploits are available.
CVE-2020-17049
Microsoft Kerberos Security Feature Bypass Vulnerability
Microsoft
|
A security feature bypass vulnerability exists in the way Key Distribution Center (KDC) determines if a service ticket can be used for delegation via Kerberos Constrained Delegation (KCD). To exploit the vulnerability, a compromised service that is configured to use KCD could tamper with a service ticket that is not valid for delegation to force the KDC to accept it. |
CVSSv3BaseScore:7.2(AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H) |
11/11/2020 |
11/23/2020 |
CVE-2020-17530
Apache Struts OGNL Remote Code Execution Vulnerability
Apache
|
A vulnerability exists in the "forced OGNL evaluation on raw user input in tag attributes" of Apache Struts. Due to insufficient validation of user input in OGNL evaluation functionality, an unauthenticated user can exploit this flaw leading it to remote code execution vulnerability. |
CVSSv3BaseScore:9.8(AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) |
12/10/2020 |
01/15/2021 |
CVE-2020-17140
Microsoft Windows SMB Information Disclosure Vulnerability
Microsoft
|
Microsoft Windows is exposed to SMB information disclosure vulnerability where an attacker can successfully exploit this vulnerability to access contents of Kernel memory. An attacker could read the contents of Kernel memory from a user mode process. In a network-based attack, an authenticated attacker would need to open a specific file with captured oplock lease, then perform repeated specific modifications to that file. |
CVSSv3BaseScore:8.1(AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:H) |
12/09/2020 |
12/11/2020 |
CVE-2020-17143
Microsoft Exchange Information Disclosure Vulnerability
Microsoft
|
Microsoft Exchange Server is exposed to information disclosure vulnerability that could be disclosed if an attacker successfully exploited this vulnerability for sensitive information. |
CVSSv3BaseScore:8.8(AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H) |
12/09/2020 |
12/11/2020 |
CVE-2020-4006
VMware Workspace One Access Command Injection Vulnerability
VMware
|
VMware Workspace One Access is exposed to a command injection vulnerability in the administrative configurator that could allow a malicious actor with network access to the administrative configurator on port 8443 and a valid password for the configurator admin account to execute commands with unrestricted privileges on the underlying operating system. |
CVSSv3BaseScore:9.1(AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H) |
11/23/2020 |
12/10/2020 |
CVE-2020-15257
containerd Privilege Escalation Vulnerability
Multi-Vendor
|
The containerd-shim API is improperly exposed to host network containers. Access controls for the shim's API socket verified that the connecting process had an effective UID of 0, but did not otherwise restrict access to the abstract Unix domain socket. This would allow malicious containers running in the same network namespace as the shim, with an effective UID of 0 but otherwise reduced privileges, to cause new processes to be run with elevated privileges. |
CCVSSv3BaseScore:5.2(AV:L/AC:L/PR:L/UI:N/S:C/C:L/I:L/A:N) |
11/30/2020 |
12/09/2020 |
CVE-2020-26258
XStream Server-Side Forgery Request Vulnerability
Multi-Vendor
|
A Server-Side Forgery Request vulnerability exists in XStream that can be activated when unmarshalling. The vulnerability may allow a remote attacker to request data from internal resources that are not publicly available only by manipulating the processed input stream. |
CVSSv3BaseScore:7.7(AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N)/td> |
12/15/2020 |
01/08/2021 |
|
|
|

