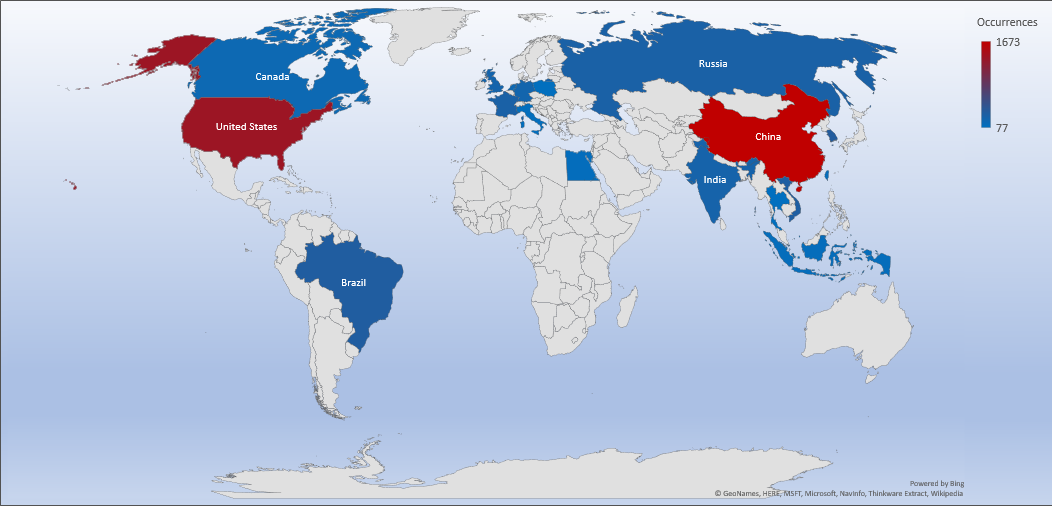
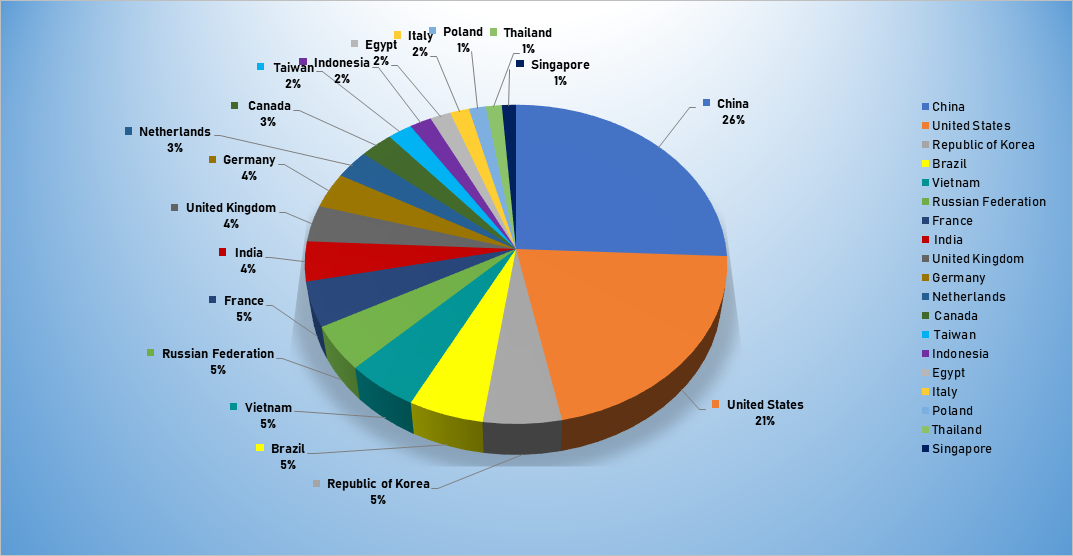
Trends
- The top attacker country was China with 1673 unique attackers (26%).
- The top Exploit event was Authentication with 44% of occurrences.
- The top Trojan C&C server detected was KeitaroTDS with 128 instances detected.
Top Attacker by Country
| Country | Occurrences | Percentage |
|---|---|---|
| China | 1673 | 25.71% |
| United States | 1373 | 21.10% |
| Republic of Korea | 357 | 5.49% |
| Brazil | 343 | 5.27% |
| Vietnam | 330 | 5.07% |
| Russian Federation | 297 | 4.56% |
| France | 296 | 4.55% |
| India | 262 | 4.03% |
| United Kingdom | 241 | 3.70% |
| Germany | 235 | 3.61% |
| Netherlands | 190 | 2.92% |
| Canada | 182 | 2.80% |
| Taiwan | 134 | 2.06% |
| Indonesia | 120 | 1.84% |
| Egypt | 113 | 1.74% |
| Italy | 104 | 1.60% |
| Poland | 93 | 1.43% |
| Thailand | 87 | 1.34% |
| Singapore | 77 | 1.18% |
Threat Geo-location
Top Attacking Hosts
| Host | Occurrences |
|---|---|
| 31.52.181.224 | 164 |
| 218.92.1.131 | 145 |
| 112.85.42.237 | 87 |
| 218.92.0.210 | 51 |
| 49.88.112.71 | 50 |
| 112.85.42.194 | 49 |
| 218.92.0.138 | 32 |
| 46.101.43.235 | 27 |
Top Network Attackers
| Origin AS | Announcement | Description |
|---|---|---|
| AS2856 | 31.48.0.0/13 | British Telecommunications PLC |
| AS4134 | 218.92.0.0/16 | CHINANET Jiangsu Province Network |
| AS4837 | 112.80.0.0/13 | China Unicom Jiangsu Province Network |
Top Event NIDS and Exploits
Top Alarms
| Type of Alarm | Occurrences |
|---|---|
| Bruteforce Authentication | 1941 |
| Network Discovery | 29 |
| Network Anomaly | 18 |
Comparison from last week
| Type of Alarm | Occurrences |
|---|---|
| Bruteforce Authentication | 30 |
| Network Discovery | 9 |
| Network Anomaly | 6 |
Remote Access Trojan C&C Servers Found
| Name | Number Discovered | Location |
|---|---|---|
| Arkei | 1 | 185.212.129.171 |
| Azorult | 3 | 185.173.176.34 213.159.208.51 8.208.11.27 |
| BetaBot | 1 | 5.45.73.113 |
| CryptBot | 1 | 213.159.209.169 |
| KeitaroTDS | 128 | 109.234.34.64, 109.234.39.39, 109.237.108.158, 109.237.110.29, 109.248.202.30, 134.0.115.146, 134.0.115.60, 134.0.116.106, 134.0.116.183, 134.0.117.113, 134.0.117.41, 134.0.119.180, 149.154.71.82, 151.248.112.91, 151.248.114.187, 151.248.122.72, 176.113.83.131, 176.53.161.105, 176.53.161.220, 176.53.162.39, 176.53.163.121, 176.57.215.15, 176.57.217.159, 176.99.11.54, 176.99.11.72, 176.99.12.144, 176.99.12.228, 176.99.12.7, 178.21.10.169, 178.21.10.226, 185.117.155.45, 185.148.82.254, 185.178.44.106, 185.179.188.137, 185.179.188.152, 185.179.188.168, 185.179.188.170, 185.179.188.172, 185.179.188.178, 185.179.188.190, 185.179.188.205, 185.179.188.207. 185.179.188.209, 185.179.188.21, 185.179.188.232, 185.179.188.250, 185.179.188.66, 185.179.188.85, 185.179.188.94, 185.179.188.97, 185.179.188.98, 185.179.190.102, 185.179.190.103, 185.179.190.147, 185.179.190.148, 185.179.190.152, 185.179.190.153, 185.179.190.157, 185.179.190.158, 185.179.190.178, 185.179.190.195, 185.179.190.38, 185.179.190.41, 185.179.190.73, 185.179.190.96, 185.20.224.222, 185.20.224.54, 185.20.225.208, 185.93.109.185, 188.120.238.25, 188.120.248.52, 188.120.253.42, 188.127.239.60, 188.225.24.2, 188.225.26.108, 188.225.26.120, 188.225.26.84, 188.225.37.94, 188.225.38.93, 188.225.76.123, 188.68.210.126, 188.93.211.127, 188.93.211.64, 193.124.181.114, 193.124.18.182, 193.124.188.96, 193.124.200.12, 193.124.200.174, 193.124.200.57, 193.124.200.74, 193.124.201.227, 193.124.201.228, 193.124.204.245, 193.124.204.57, 193.124.204.79, 193.124.204.88, 193.124.206.143, 193.124.207.184, 193.124.207.19, 193.124.44.234, 193.124.44.55, 193.124.93.237, 193.176.78.64, 194.113.107.118, 194.113.107.139, 194.147.35.176, 194.58.100.158, 194.58.104.26, 194.58.107.70, 194.58.108.51, 194.58.111.35, 194.58.119.193, 194.58.122.56, 194.58.38.175, 194.58.38.190, 194.58.38.199, 194.58.38.204, 194.58.39.109, 194.58.39.215, 194.58.40.228, 194.58.40.235, 194.58.47.158, 194.67.87.251, 194.87.202.71, 31.31.201.47, 46.254.21.24, 5.23.55.239, 92.63.192.143 |
| LokiBot | 2 | 185.173.179.13 185.87.187.198 |
| ParasiteHTTP | 1 | 5.45.73.113 |
| Pony | 1 | 94.102.53.52 |
| PredatorTheThief | 48 | 109.94.110.157, 139.180.223.36, 178.62.188.204, 178.62.191.13, 178.62.191.173, 18.222.210.14, 18.222.227.101, 18.225.10.183, 185.14.186.39, 185.146.156.38, 185.193.126.123, 185.206.144.170, 185.244.217.108, 185.254.121.122, 185.254.121.126, 185.254.121.141, 185.254.121.161, 185.60.133.242, 190.97.167.143, 190.97.167.238, 192.81.220.183, 193.124.117.116, 193.37.212.107, 213.159.209.1, 2.56.214.102, 31.184.197.158, 3.15.40.147, 37.139.2.42, 45.10.219.20, 45.10.219.7, 45.12.212.187, 45.12.213.98, 46.101.160.184, 46.249.62.207, 47.89.189.85, 5.101.180.213, 51.15.228.96, 5.196.214.131, 79.124.8.105, 81.177.180.205, 8.208.9.124, 82.196.1.19, 82.196.9.220, 82.202.163.189, 83.220.174.244, 92.63.192.138, 92.63.192.144, 92.63.192.221 |
| TrickBot | 38 | 107.172.201.144, 107.174.71.44, 146.185.219.21, 178.170.189.117, 185.117.73.58, 185.142.99.39, 185.172.129.11, 185.183.99.159, 185.202.174.77, 185.241.53.109, 192.210.226.104, 193.124.185.113, 194.87.111.102, 195.123.233.35, 195.123.237.126, 195.123.238.54, 198.12.97.170, 198.12.97.204, 198.46.198.103, 198.46.198.12, 198.46.198.132, 212.80.217.182, 31.184.253.244, 37.228.117.142, 50.3.68.150, 51.79.57.148, 54.36.24.100, 54.37.195.102, 5.53.124.147, 5.53.124.49, 5.9.178.87, 79.143.31.94, 80.87.199.54, 81.177.136.17, 82.146.43.15, 89.105.203.182, 91.235.129.80, 94.103.95.91 |
Common Malware
| Malware Type | MD5 | Typical Filename |
|---|---|---|
|
PUA.Osx. |
125ef5dc3 115bda09d 2cef1c5086 9205 |
PUA.Osx. |
|
Win.Trojan. |
47b97de62 |
Win.Trojan. Generic:: in10.talos |
|
Unix.Exploit. |
f7145b132 |
Unix.Exploit. |
|
W32.39A87 |
df61f1384 |
W32.39A87 5089A- 100.SBX.TG |
| W32.7ACF7 1AFA8- 95.SBX.TG |
4a50780d |
W32.7ACF7 1AFA8- 95.SBX.TG |
CVE
This is a list of recent vulnerabilities for which exploits are available.
ID: CVE-2019-1181
Title: Microsoft Remote Desktop Services Remote Code Execution Vulnerability
Vendor: Microsoft
Description: A remote code execution vulnerability exists in Remote Desktop Services - formerly known as Terminal Services - when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests. To exploit the vulnerabilities, an attacker would need to send a specially crafted request to the target systems Remote Desktop Service via RDP. More information is available - "https://blog.qualys.com/laws-of-vulnerabilities/2019/08/13/windows-remote-desktop-vulnerabilities-seven-monkeys-how-to-detect-and-patch". This CVE ID is unique from CVE-2019-1181, CVE-2019-1222, CVE-2019-1226.
CVSS v2 Base Score: 10.0 (AV:N/AC:L/Au:N/C:C/I:C/A:C)
ID: CVE-2019-1222
Title: Microsoft Remote Desktop Services Remote Code Execution Vulnerability
Vendor: Microsoft
Description: A remote code execution vulnerability exists in Remote Desktop Services - formerly known as Terminal Services - when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests. To exploit the vulnerabilities, an attacker would need to send a specially crafted request to the target systems Remote Desktop Service via RDP. More infromation is available - "https://blog.qualys.com/laws-of-vulnerabilities/2019/08/13/windows-remote-desktop-vulnerabilities-seven-monkeys-how-to-detect-and-patch". This CVE ID is unique from CVE-2019-1181, CVE-2019-1182, CVE-2019-1222.
CVSS v2 Base Score: 10.0 (AV:N/AC:L/Au:N/C:C/I:C/A:C)
ID: CVE-2019-5994
Title: EOS Camera Picture Transfer Protocol Memory Corruption Vulnerability
Vendor: Canon EOS
Description: A Buffer overflow vulnerability exist in PTP (Picture Transfer Protocol) of EOS series digital cameras that allows an attacker on the same network segment to trigger the affected product being unresponsive or to execute arbitrary code on the affected product via SendObjectInfo command.
CVSS v2 Base Score: 6.4 (AV:N/AC:L/Au:N/C:P/I:N/A:P)
ID: CVE-2019-0193
Title: Apache Solr Remote Code Execution Vulnerability
Vendor: Apache
Description: A vulnerability exists in the DataImportHandler module of Apache Solr, a common module used to import data from databases or other sources. The whole DIH configuration of this module can come from the dataConfig parameter included in an external request. An attacker could exploit this vulnerability to cause arbitrary code execution via a malicious request that contains a carefully crafted dataConfig parameter.
CVSS v2 Base Score: 9.0 (AV:N/AC:L/Au:S/C:C/I:C/A:C)
ID: CVE-2019-14234
Title: Django Index lookup SQL Injection Vulnerability
Vendor: Django
Description: Due to an error in shallow key transformation, key and index lookups for django.contrib.postgres.fields.JSONField, and key lookups for django.contrib.postgres.fields.HStoreField, were subject to SQL injection. A remote attacker could possibly use this issue to perform SQL injection attacks.
CVSS v2 Base Score: AV:N/AC:L/Au:N/C:N/I:N/A:P Base Score: 5