
Seven people between the ages of 16 and 21 have been arrested by London City police in connection with a hacking group (Lapsus$) investigation. One of the ones arrested is a 16-year-old from Oxford who is believed to be one of the leaders of the Lapsus$ group.
“White” as the 16-year-old was known as online, Was doxxed on a hacker website after an apparent falling out with business partners. It is believed after a few years of hacking and extortion that his net worth has accumulated well over 300BTC ($17.5 million). This comes only a few days after the Okta and Samsung hack.
The hacking group Lapsus$ has claimed to have hacked Okta, the San Francisco based company that provides secure user authentication systems. The hack is related to a security incident that occurred in late January 2022.
The Lapsus$ group is a South American based extortion group that has targeted many major companies such as Microsoft, Vodafone, NVIDIA, Samsung and many others. Lapsus$ is known to target outdated software, weak security practices and insider information to secure stolen data and hold the target to ransom to avoid the data being released online to the public. Lapsus$ group has claimed that they were not after the Okta themselves, but rather its customers.
Okta provides Identity-as-a-Service which allows software, website and devices to easily implement Single Sign-On (SSO) and Multi-Factor Authentication (MFA). Okta previously made a statement that they were aware of a security incident that occurred in January but said any attempt to compromise an account was unsuccessful. They have later come out and said 2.5% of its customer base could now be affected by the hack.
The hack allegedly occurred when Lapsus$ got access to a support engineer’s laptop which gave them internal access to Okta’s admin systems. The images below were posted by Lapsus$ group as a proof of compromise of Okta's systems.
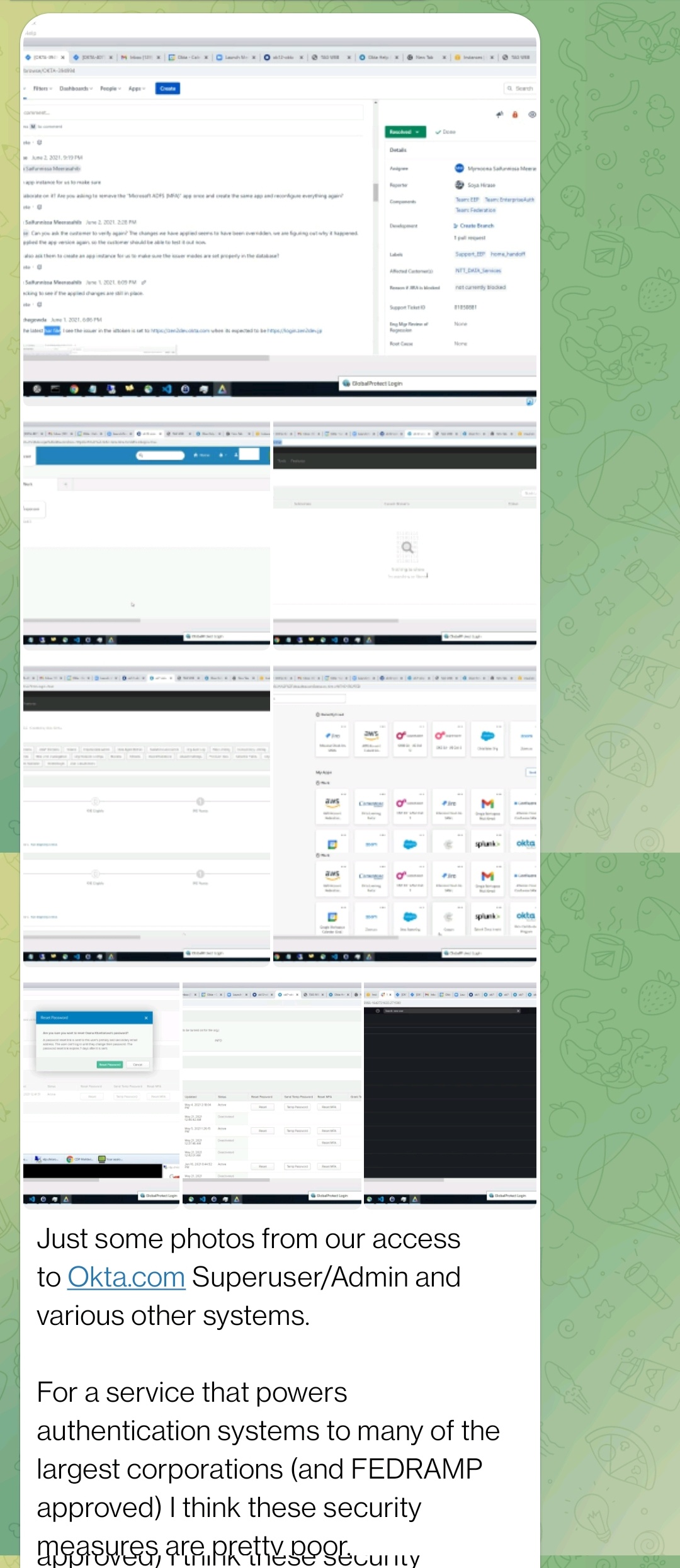
Mitigation
If you are an Okta customer, we advise the following actions:
- Enable MFA for all user accounts. Passwords alone do not offer the necessary level of protection against attacks. We strongly recommend the usage of hard keys, as other methods of MFA can be vulnerable to phishing attacks.
- Check all password and MFA changes to your Okta instances.
- Pay special attention to support-initiated events.
- Make sure all password resets are valid or just assume they are all under suspicion and force a new password reset.
- If you find any suspicious MFA-related events, make sure only valid MFA keys are present in the user's account configuration.
- Make sure you have other security layers to provide extra security in case one of them fails.
